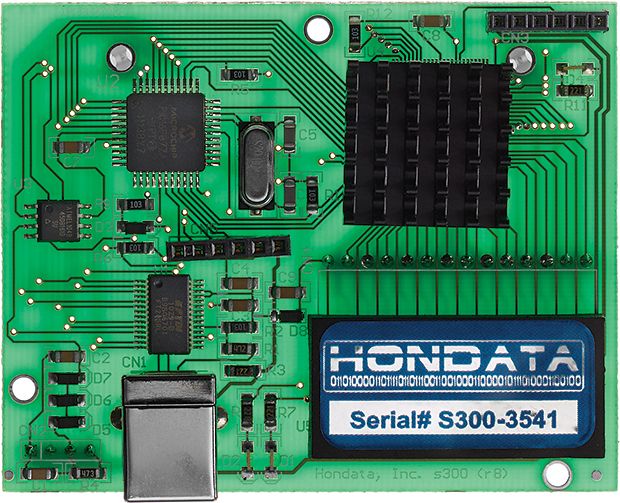
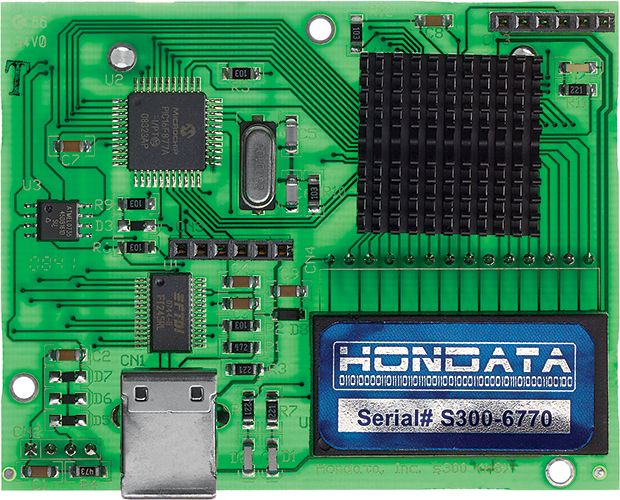
In February 2014, the FBI charged a Florida man, Marc Heera, with selling a cloned version of the Hondata s300, a plug-in module for the engine computer that reads data from sensors in Honda cars and automatically adjusts the air-fuel mixture, idle speed, and other factors to improve performance.
The plug-in also allows users to monitor the engine via Bluetooth and make their own adjustments. The clones certainly looked like the genuine product, but in fact they contained circuit boards that had likely been built in China, according to designs Heera had obtained through reverse engineering. Honda warned that cars using the counterfeits exhibited a number of problems, including random limits on engine rpm and, occasionally, failure to start. Devices that connect to an engine control unit (ECU) present particular safety concerns; researchers have demonstrated that, through ECU access, they could hijack a car’s brakes and steering.
It’s not just car parts that are being cloned; network routers and parts for routers are also popular targets for cloners. That may not sound particularly scary until you consider that a hacker who has control of a cloned router can then intercept or redirect communications on the network. Look at the 2010 case of Saudi citizen Ehab Ashoor, who was convicted of purchasing cloned Cisco Systems gigabit interface converters with the intent to sell them to the U.S. Department of Defense. The devices were to be installed in Iraq in Marine Corps networks used for security systems and for transmitting troop movements and relaying intelligence from remote field operations to command centers.
While Ashoor appears to have been motivated by greed rather than any desire to do harm, the impact of ersatz equipment in critical electronic systems like a secure router or a car’s engine can still be catastrophic, regardless of the supplier’s intent.
And unlike counterfeit electronics of the past, modern clones are very sophisticated. Previously, counterfeiters would simply re-mark or repackage old or inferior components and then sell them as if they were new and top of the line; the main problem with these knockoffs was poor reliability. Cloned electronics these days are potentially more nefarious: The counterfeiters make their own components, boards, and systems from scratch and then package them into superficially similar products. The clones may be less reliable than the genuine product, having never undergone rigorous testing. But they may also host unwanted or even malicious software, firmware, or hardware—and the buyer may not know the difference, or even know what to look for.
Installing cloned hardware into networks, for instance, could open the door to hackers: They could launch man-in-the-middle attacks or secretly alter a secure communication path between two systems in order to bypass security mechanisms, like integrity verification, encryption, and end-point authentication. Software hidden in a router could allow an attacker to take control of other systems on the network, rerouting data to remote servers or even disrupting critical systems, such as the flow of electricity through a smart grid. A cloner who succeeds in embedding malicious software or hardware into a combat drone could shut it down or retarget it when it reached preset GPS coordinates.
Already, entire lines of consumer electronics have been cloned. Back in 2004, the Japanese electronics giant NEC Corp. received reports from Beijing and Hong Kong that pirates were selling keyboards, CDs, and DVDs bearing the company’s logo. When NEC investigated further, it discovered the problem was far worse: The cloners had developed a host of consumer electronic products—including home entertainment systems, MP3 players, batteries, microphones, and DVD players—and then sold them under the NEC label. The cloners even provided official-looking warranty documents to customers.
While there appear to be no published reports of injury or hacking related to this cloning, the risks are bigger today because more of the systems we interact with daily are connected to the Internet of Things. Cloned hardware may lack the security modules intended to protect such devices, and so it opens up the unsuspecting user to cyberattack.
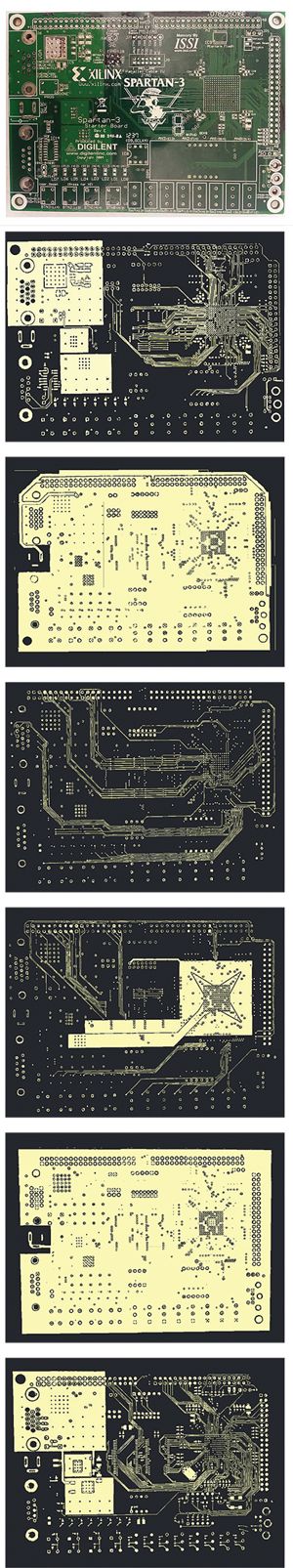
Cloning spans all levels of electronics. Cloning a printed circuit board (PCB) can be relatively straightforward, particularly if the cloner is able to use off-the-shelf components. By contrast, cloning an integrated package of electronics such as a network router requires obtaining the details of all the parts as well as any embedded firmware, manufacturing or purchasing each part, and then assembling them into a functional product.
And cloning microchips, especially today’s billion-transistor versions, is even more challenging. A chip becomes an attractive target for cloners only if the market demand is high enough to make it worth the effort. That can happen when a manufacturer stops producing a particular chip, thus forcing anyone who wants to use the discontinued chip to buy it through a distributor that still has stock. As time goes on, the chip will become scarce. Consider two Texas Instruments microprocessors with essentially the same specifications: The discontinued XOMAP3525BCBB lists for US $72, and the still-manufactured OMAP3515ECBBA lists for $52. As the price of the discontinued chip continues to climb, at some point cloners may be willing to make the investment in reverse engineering the original chip. Or, if they get their hands on a pirated design file, they can produce a clone without a big investment.
Nobody really knows the true scale of electronics cloning, thanks to the clandestine nature of the activity and the lack of adequate detection measures in the global supply chain. But we can infer the size of the market by extrapolating from the cloned products that are seized each year by police and customs authorities.
Using this kind of extrapolation, the International Chamber of Commerce estimated that trade in counterfeit and cloned products—including nonelectronic products such as designer handbags—amounted to $650 billion globally in 2011. The ICC projected that the figure would nearly triple, to $1.7 trillion, by the end of 2015. (The organization does not track electronics separately.)
Estimates do exist for certain types of electronics. In 2005, for example, the FBI, U.S. Immigration and Customs Enforcement, and U.S. Customs and Border Protection kicked off Operation Network Raider, an international initiative to control the illegal distribution of fake network hardware. Between 2005 and 2010, the campaign led to 30 felony convictions and the seizure of nearly $143 million worth of fake network hardware; similar efforts leading to arrests and equipment seizures continued after that campaign ended, but the numbers haven’t been aggregated.
Whatever the true size of the cloned electronics market, we are sure that it is growing, based on our work with SMT Corp., whose labs specialize in identifying cloned and counterfeited components in global supply chains. Among the trends contributing to the growth of cloning are more-sophisticated imaging and analysis tools—we’ll discuss these in a moment—and the spread of contract manufacturing, a business model in which the companies that design chips and systems outsource their fabrication. As design files are passed back and forth between the designer and the contractor, cloners will exploit any crack in security to get those files. Once a cloner succeeds in fabricating credible copies, the ubiquity of online sales makes it easy for the sellers to hide their identities and attract bargain-minded customers.
So who exactly are the cloners? They could be just a couple of guys in a garage or a big state-funded organization, or something in between. State-sponsored cloning is thought to be common. Cloners in some countries argue that they don’t trust U.S. manufacturers, so they clone U.S. chips to make sure their chips are free of deliberately implanted malicious circuits—sometimes called hardware Trojans. A side benefit is that the fake chips come with no licensing fees. These clones can and do get onto the international market.
Regardless of who’s doing the cloning, they generally follow a two-step process: First, they copy a design, and second, they fabricate the product. The cloners may secretly buy the design from an employee at the target company, or they may hack into a computer containing that information.
A slightly more sophisticated approach is to reverse engineer the intended product. This kind of work has gotten much easier in the past two decades. The advent of better and cheaper imaging instruments and analysis tools have enabled reverse engineering of even the most complex microchips. Today’s optical microscopes can produce 3D images of a chip with superfine resolution. Scanning electron microscopes and transmission electron microscopes can image the microchip’s inner layers; high-resolution digital X-ray machines do the same for PCBs. Reverse-engineering companies like TechInsights (which recently acquired Chipworks) use this kind of imaging legitimately for the purposes of competitive analysis and patent research.
The other type of reverse engineering involves taking the product apart to understand how it’s made. Using chemical etching, for instance, a cloner can remove each layer of a chip or PCB. Unlike the technique using high-end microscopes and X-ray machines mentioned above, this process requires only a low-power optical microscope to view the result. But the cloner might have to go through 50 or more chips or PCBs to get the design right.
In system-level cloning, such as that needed to reproduce routers and other network hardware, cloners may use some form of reverse engineering, or they may buy the design details from a friendly source at the manufacturer, along with stray parts or products that failed testing. But to complete the clone design, they also need to install firmware—the basic programs used to tell the system how to operate. Firmware for a router might include information such as what frequency the router communicates over or what type of security protocols it uses. On most PCBs, the system firmware is stored in nonvolatile memory—ROM, EEPROM, or flash. A cloner can copy it during the power-up cycle, by tapping a data bus when the processing unit loads system instructions from nonvolatile storage into active memory. Alternatively, the cloner can look directly at the memory itself, using a scanning electron microscope or infrared backside imaging; the latter takes advantage of the fact that semiconductor materials are transparent to certain wavelengths of light. Under a powerful microscope, the cloner can actually see the stored 1s and 0s and reconstruct the code.
Finally, to fabricate the fake, the cloner typically turns to an independent manufacturing facility, which may be similar to or even the same as that used to make the genuine product. Occasionally, cloners use their own production lines, but that’s an expense few cloners can afford.

Fighting back against the cloners isn’t easy, given the wide variety of electronic products that can be copied and the multitude of ways cloners use to get the job done. To date, the main defense has involved supply-chain security—essentially, giving each chip, PCB, and product a unique identification number to allow it to be tracked throughout the supply chain, from the manufacturer to the end user. That tactic, however, has proven of little value. The ID numbers are maintained in open databases so that companies can verify them. Cloners can simply access the databases, copy the ID numbers, and then place them on their counterfeit goods. Supply chains are so complicated that it’s impossible to distinguish between a legitimate company making a database query and a cloner stealing IDs.
So researchers in academia, government, and industry have been working on other approaches. One tactic involves tagging chips and circuit boards with special materials, such as plant DNA. Clone fighters take botanical DNA sequences and scramble them, creating unique patterns that can be used as a signature for a batch of electronic parts. They then mix this DNA with selected fluorophores, which are chemicals that glow under specific wavelengths of light, and tag the electronics with this DNA ink.
Purchasers trying to confirm whether a chip is authentic will scan it for the fluorescent signature; if it’s missing, it’s a sure indication that something is wrong. If the fluorescent mark exists, the purchaser will swab the spot to pull a sample of the DNA and then send it to a lab. Standard forensic DNA techniques are used to identify the plant sequences, which get checked against the product’s database to confirm whether the label and the part matches.
According to Janice Meraglia at Applied DNA Sciences, one of the companies that offer DNA authentication, DNA tagging is pretty much clone proof. The DNA sequence data is held in a database that is accessible only to laboratory staff, unlike the open databases used for traditional parts IDs. Cloners also don’t have access to an essential element of the DNA tagging process: the primer required to start the chain of DNA formation. Primers are small, custom-built sequences of DNA to which other specific sequences of DNA attach; they basically help DNA sequencing tools find the start of the DNA chain.
The downsides of DNA tagging are its expense and how long it takes for authentication. Right now, the list price of a single test is $250, according to Meraglia; this cost drops when an organization signs on for a regular supply-chain testing program. And, she says, the company is working on test equipment that could be used at a parts purchaser’s location to reduce the time lag, turning tests around in under an hour.
These issues have kept the technique from becoming widely adopted, but some U.S. government agencies have already begun to tag critical electronic parts. Meraglia thinks the technology will soon move into the financial services industry to verify critical parts of its infrastructure, such as the routers that move data.
The latest promising countermeasure against electronics cloning is something called the physical unclonable function (PUF), which can potentially protect chips, PCBs, and even high-level products like routers. PUFs give each chip a unique “fingerprint.” They rely on the physical variations among transistors or other components on a chip, like the width of metal traces, which in turn cause subtle differences in behavior.
The behavior most often exploited by PUF designers is the variation among switching speeds of different transistors. When many transistors are combined into a circuit, the differences in their switching speeds affect the signal propagation along a specific path, which can be measured and compared with the signal propagation of another, supposedly identical path on the same chip. From the two paths, the manufacturer can create a 1-bit signature for the chip. For example, if the switching speeds are faster along the first path than the second one, the manufacturer can assign the bit as “1.” To create a longer signature—say, 16 or 64 bits—it typically compares more paths.
The PUF paths must be designed into the chip, either making use of existing features on the chip, such as test circuits or embedded memory, or by building in dedicated circuitry. Once a batch of chips is manufactured, the chipmaker checks how the PUF structures on each chip respond to specific inputs generated by external or internal test circuitry, and then registers the chip’s unique signature in a database. A customer can query the database to see if a chip at any phase in the supply chain is authentic or fake, in much the same way a database containing biometric fingerprints can be checked to identify a person.
Because PUF fingerprints are determined during the manufacturing process, they are extremely difficult to replicate. But they suffer from several problems that have prevented their widespread adoption. The first is instability. The tiny variations in transistors that underlie the chip’s digital signature can fluctuate along with the supply voltage or the ambient temperature. And as a transistor ages, its switching speed can slow down.
These problems can be addressed to some extent by increasing the number of signatures used for each chip. In this way, a chip can be recognized based on a less-than-perfect match over a large number of signatures; when it comes to detecting clones, a 90 percent match for 100 signatures may be as good as or better than a perfect match for just one signature. But nobody has yet figured out a way to avoid unstable signatures altogether.
Another problem with PUFs is their cost, which results from the additional design time, any new circuitry that needs to be included, and the signature-gathering from the finished chip. PUF technologies that rely on existing chip components—such as embedded memory or test structures to generate the signatures—will add little or no cost to the design.
A final problem is that cloners could use statistical modeling to predict the behavior [PDF] of some PUFs. Researchers have demonstrated that signatures from some PUF technologies aren’t as random as initially thought, and therefore chips with those types of PUFs aren’t protected from being cloned.
Despite these concerns, some companies, including Microsemi Corp. and Xilinx, have started to use PUFs for chip identification. And researchers have been extending the concept to printed circuit boards. In this case, they use random variations inside the chips that go onto the PCB as well as variations in the metal traces that connect them. This approach is particularly exciting because, unlike chip fingerprints, PCB fingerprints can be checked remotely to verify the authenticity of a piece of equipment. So the technique could be used, for example, to ensure that critical infrastructure components, once installed, aren’t later replaced with clones.
Research on advanced methods for clone detection is just beginning. Government and industry will need to pay more attention to this issue, as powerful reverse-engineering tools become cheaper and more accessible to would-be cloners.
And as the number of Internet of Things devices grows, everyone should become more aware of the dangers that cloned products pose. Some industry projections estimate the IoT population could reach 30 billion by 2020. Imagine if just 1 percent of those connected devices were clones harboring malicious hardware or software. That would mean a potential army that’s 300 million strong, waiting for the opportunity to launch an attack of the clones.




